VMRay Action for ThreatQuotient TDR Orchestrator
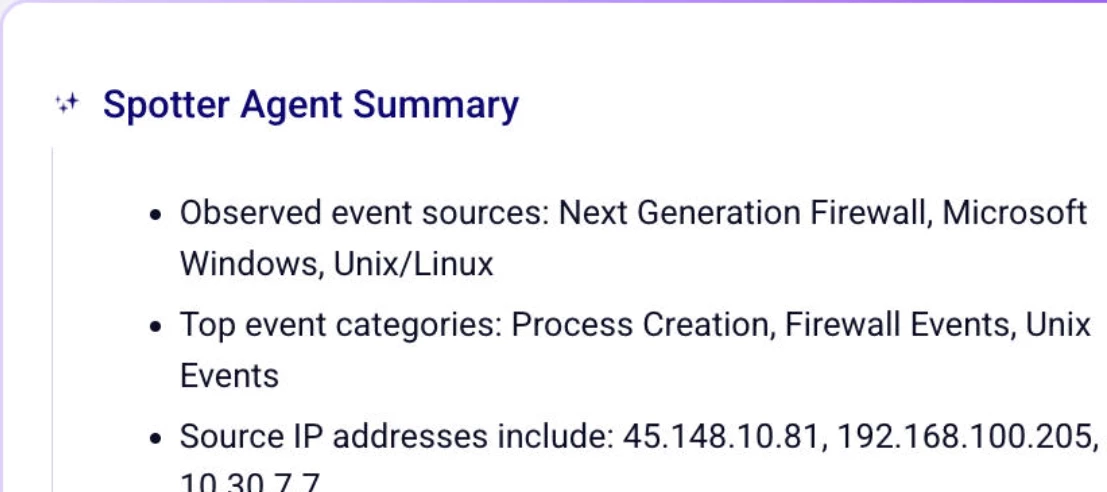
🧠 OverviewWe’re thrilled to announce the release of the VMRay Action for the ThreatQuotient TDR Orchestrator!This new integration allows you to submit URL-based data collections directly to the VMRay Malware Analysis Platform for dynamic analysis and enrichment. By automating the submission of indicators of compromise (IOCs) to VMRay, analysts can enhance detection accuracy and streamline threat investigation workflows.⚙️ Key CapabilitiesThe integration introduces a new TDR Orchestrator Action:VMRay – Submit IOCs – Exports IOCs (specifically URL objects) from ThreatQ to the VMRay platform for automated analysis and enrichment.Once submitted, VMRay returns enriched URL-type indicators that can include:Verdicts (e.g., malicious, suspicious, benign) IOC metadata YARA rule matches Behavioral and network indicators Malicious file hashes Detonation reports (PDF format)🔌 VMRay Operation Connection CapabilitiesThe VMRay Operation enables direct connection from ThreatQ into the VMRay Analyzer to:Submit URLs, FQDNs, and file objects for sandbox detonation. Retrieve structured analysis results for deeper threat correlation. Integrate verdicts and intelligence artifacts into ThreatQ collections for continued investigation.💡 Use CasesSome key use cases for this integration include:Enhanced Threat Intelligence: Automatically enrich IOCs with sandbox verdicts. IOC Mining: Discover new related indicators from dynamic analysis results. Secure Detonation: Analyze URLs and files in a controlled environment. Binary Evaluation: Assess unknown binaries or payloads before network exposure.🔐 RequirementsTo utilize the VMRay Action, ensure you have:An active ThreatQ TDR Orchestrator (TQO) license. Valid credentials for the VMRay Platform.